Secure Remote Access Solutions
Remote or hybrid working models have become very popular these days. One can work from anywhere by using a laptop or computer. For remote or hybrid working models, secure remote access is needed. Secure remote access is a wider term. It refers to security measures, policies, and technologies used to deliver network, device and application access from an outside location. Remote access allows you to use the resource without visiting the location from an outside area. In other words, use a home or public Wi-Fi connection to connect to a data center, network, applications, or cloud resources using a remote device.
Secure remote access solutions are needed by organizations who offer remote or hybrid working to establish remote connection with less risk of unauthorized access. Use of technologies and policies for remote access may vary for the different organizations as per their needs and budget. TechyBizz offers secure remote access solutions for every business as per need & budget to establish secure connection. We protect your data from being used by unauthorized access points and offer a more secure working environment.
Why is a secure remote access solution needed?
Advantages of Secure Remote Access
- Allows you to hire employees from across the globe for your organization.
- Employees can work from anywhere without wasting their time in getting stuck in the traffic to reach the office.
- Don’t need an infrastructure for your business as your employees work remotely.
- Allow employees to use data or files they need without visiting office premises in a hybrid working model.
- Security for data and protection from unauthorized access.
- Better remote access solutions increase the productivity of employees.
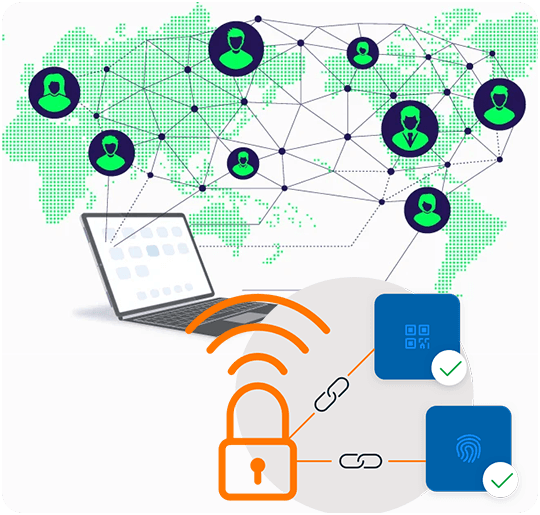
Technology used for Secure Remote Access
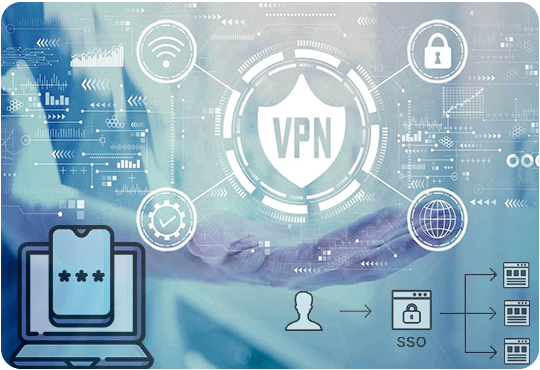
VPN
VPN is also known as Virtual Private Network is the primary concern to offer Secure Remote Access Solutions. Through VPN a tunnel between the remote user & network has been created that provides access. Users need authentication prior to using the network. Once the access is granted, there is no restriction on use of the network.
2FA/MFA
Two-Factor/Multifactor Authentication is a method which is used by a user to use the network after getting authentication from at least 2 means. In this technology any combination of password, email address, remote desktop, mobile device, or even biometrics such as a fingerprint can be used. Only if the user gets authenticated from all means then access will be permitted otherwise denied even if any one of them fails.
SSO
SSO (Single sign-on) technology is very often used. Here only one-time authentication is required to get the access. This technique is used to avoid managing several passwords.
PAM
Privileged Access Management is a method to give remote access only to the particular resource you are authorized to use. This method gives IT professionals greater visibility to monitor accounts in real time. This method is appropriate to protect from cyberattacks and insider threats.
Why choose TechyBizz?
- Our team members have IT experts with years of experience.
- Our service standards are high.
- We are the most trusted IT partner in the industry.
- We keep your data safe & secure.
- Our service packages are pocket friendly.
- We render secure remote access solutions.
- We provide 24*7 technical support to our clients.
- Our service supports Windows, Mac, Linux, iOS, Android, and Linux platforms.
We’re All Ears
Got a question? Need support? Just want to say hi? We’d love to hear from you.

Intimate Services
Providing trusted and reliable Information Technology Services.

"Techybizz doesn’t just fix issues—they help us avoid them in the first place. And our online presence has never been stronger."

"These guys are lifesavers! I used to dread tech problems and struggle with marketing, but now I know I’m in good hands."

"Tech can be a nightmare, and digital marketing is tough, but with Techybizz, it’s like having a dream team on speed dial."

